How to secure your APIs using Apigee

Written by Ali Akhtar
Technical Account Manager – Middleware
October 5, 2022
API Security means ensuring that your APIs are secure from unauthorized access by third parties. It also includes securing your backend systems from direct access by unauthorized users.
Apigee’s foundation was a security solution for the enterprise. The solution has since expanded and is now used by customers with sensitive security needs such as PCI (Payment Card Industry) and HIPAA (US Health Insurance Portability & Accountability Act). In spite of being a key component of a defense-in-depth security strategy, the API Service is useful for blocking traffic spikes and DOS attacks, SQL injection, Java Script Injection, XPATH injection, XSS, and malicious XML. The API Service can also be used for data masking (for testing and logging).
Apigee provides out-of-the-box policies to support Replay Threat Detection, and XML Payload protection, to prevent attacks on the Web Services and Gateway proxies. Screening against XML threats can take on various forms including validating messages against a valid schema, finding specific blacklisted keywords or patterns in messages, or detecting abnormally formed messages. For example, a malformed IP message may not break a router but can however disable the XML parser inside an Application.
Authentication
Authentication is one of the important aspects that the provider has to take into account before exposing the API to external consumption.
Apigee Edge platform supports multiple authentication mechanisms including:
- OAUTH – All versions all draft of OAuth are supported.
- SAML 2.0
- Basic HTTP Auth
- API key-based validations
- X509 certificate-based authentication
- OpenID
- OpenID connect
- Digest authentication
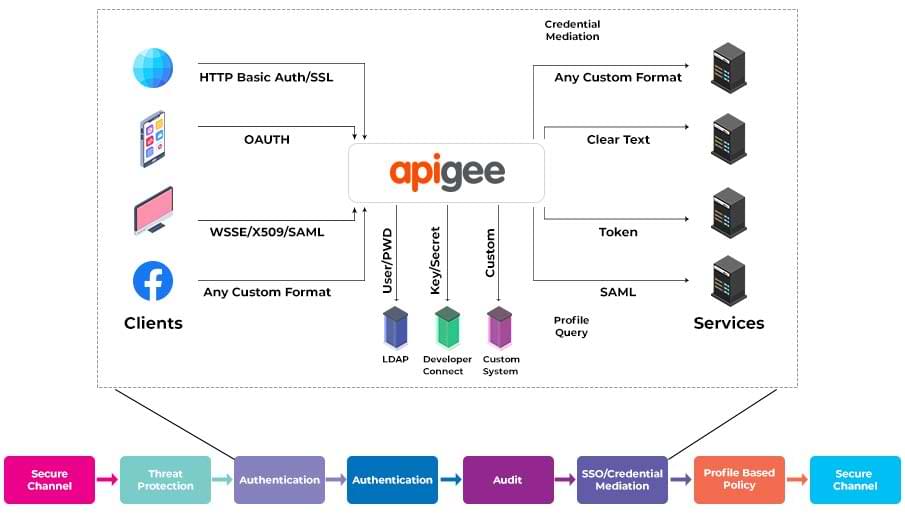
Apigee can help enforce identity on top of the API. By letting Apigee take care of enforcing Identity, Organizations can reduce the development cycles, as Apigee has full support for the common Auth schemes like OAuth 2.0, OAuth 1.0, and many other traditional Auth schemes.
Since all the requests go through Apigee, the Identity will be applied in a standard and commonplace (Apigee API Service) across all APIs. Apigee also helps many customers with Credential Mediation. This allows enterprises to expose different and newer security schemes on the north bound for developers and apps while Apigee mediates the enterprises’ existing security mechanism.
Apigee API Service could also be configured to talk to any Identity, authentication, secure token service, SSO and access control providers. Apigee can also be a service provider for SAML providers and can consume SAML tokens (sender-vouches and holder-of-key) for identification/authorization. Apigee can also do a variety of credential mediation such as SAML (as backend) to OAuth or Open ID (Backend) to OAuth to support modern devices.
Transport Layer Security (TLS), and its predecessor, Secure Sockets Layer (SSL), are key to effective Internet security and are fully supported in Apigee Edge. Two-way TLS (aka “mutual authentication” or “TLS with client certificates”) is supported for cryptographic authentication from the client to Apigee and from Apigee to the target.
Aside from enabling user management and OAuth-based login for your app, API Services also makes it simple to incorporate third-party authentication using well-known services like Facebook, Twitter, and other OAuth-enabled accounts. By allowing third-party sign-in, you can enhance user experience, boost adoption, and gain access to useful data from social networks and services.
For example, see Facebook sign-in documentation: http://apigee.com/docs/usergrid/content/facebook-sign-in
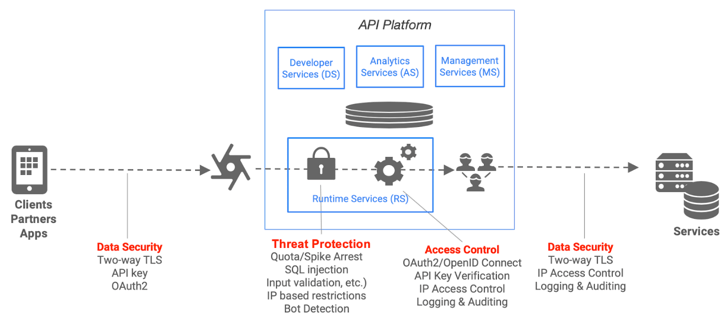
The Apigee Edge product has out-of-the-box support for managing API keys. API key generation, approval, regeneration, and revocation are supported by the API product as well as by TPA. This can be done via API Management UI or APIs.
Data Protection
Any server that receives data from the internet is vulnerable to attacks, whether intentional or not. The adaptability of XML/JSON is used by some attacks to create faulty documents that affect back-end systems. Servers may allocate more memory than is necessary for response to corrupt or overly complicated XML/JSON documents, using CPU and memory resources, crashing parsers, and overall impairing message processing and resulting in application-level denial-of-service attacks.
The API Platform enables you to enforce JSON/XML Threat Protection policies that address XML and JOSN vulnerabilities and minimize attacks on your API.
Organizations can screen against threats using the following approaches:
- Validate messages against an XML schema (.xsd)
- Evaluate message content for specific black-listed keywords or patterns
- Detect corrupt or malformed messages before those messages are parsed
Out-of-the-box threat protection policies enables organizations to protect back-end services from a variety of threats such as:
IP Based Access Control
Malicious Code Injection
Message Validation
XML Payload Attack
SQL injection
Replay Attack
In addition, Apigee’s flexible policy framework is extensible enabling the ability to implement protection policies against other vulnerabilities like traffic spikes and DOS attacks as needed. The gateway can also be used for data masking (for testing and logging).
Apigee also supports variety of techniques to protect against snooping and tampering by enabling encryption using any algorithm that any organization wants to implement or by enabling two-way SSL. TLS and SSL security are available for network transmission security. The level and algorithms used can be adjusted based on the requirements.
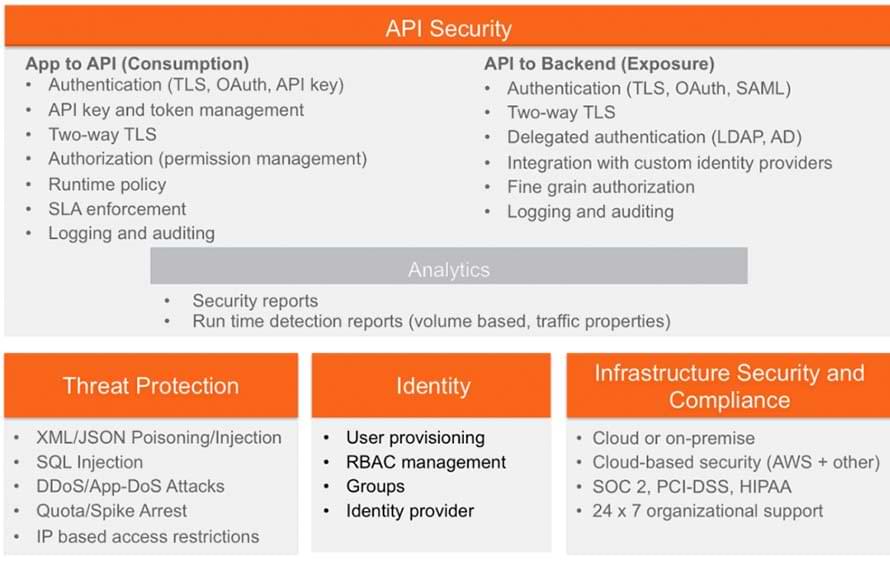
The following highlights the different security capabilities provided by the platform across several security domains.
Comprehensive App and API Security
Owasp Standards
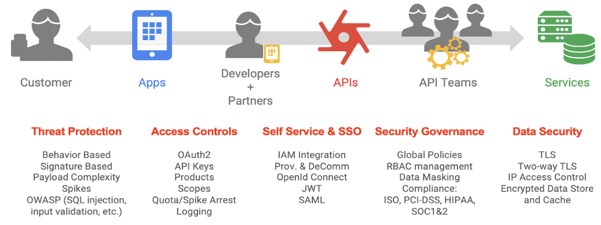
API ecosystems are subject to a variety of internal and external client threats. Service providers have a lot of benefits when they offer and use APIs, but there are also significant security threats. When creating and utilizing APIs, developers must be aware of these difficulties and take steps to overcome them.
By detecting, blocking, and reporting erroneous API requests from the client before they are handled by the backend systems, Apigee’s API proxy layer helps to reduce risk and safeguard your services. Any element that makes up the HTTP application-level protocol can be used in malformed requests:
URL
Headers
Path
Payload
Malicious bots or known or unknown clients created by outside developers, internal developers, or malformed API queries are all examples of malformed API requests. The majority of OWASP dangers come from these queries, however, there are other elements of the underlying API proxy layer that help reduce risks, like data masking, logging, management, and so forth.
When creating your APIs and integrating them with your backend systems, you can take a consumption-focused approach and seamlessly solve the top OWASP API security risks thanks to Apigee’s intelligent API management platform. The list of policies and configurations that Apigee suggests for the top REST OWASP risks is provided below.
Additionally, there are a number of methods for validating input on the Apigee platform:
- Threats are screened for in the JSON payload by JSONThreatProtection.
- Threats are screened for in the XML payload by XMLThreatProtection.
- JavaScript can be used to conduct parameter validation.
- JavaScript can be used to conduct header validation.
- Regulated expression protection can be used to deal with SQL CodeInjection.
Validate content types:
- Request – Check the Content-Type header using conditional logic in the proxy flow. To return a specific error message, use the AssignMessage or RaiseFault policies.
- Response – Check the Content-Type in the proxy flow using conditional logic. To set a Content-Type header, use the AssignMessage policy. To return a specific error message, use the AssignMessage or RaiseFault policies.
Session Management
Attackers can access passwords, session tokens, and keys to impersonate other users by taking advantage of implementation flaws in applications. This is more of an implementation problem and not a product issue. Apigee provides VerifyApiKey, OAuth, and JSON Web Token (JWT) policies, which help protect against this vulnerability.
Conclusion
Royal Cyber has vast experience in implementing APIs and securing them. We have the appropriate professionals and processes in place to support your company’s digital transformation journey thanks to our extensive experience implementing Apigee globally. For more information, you can email us at [email protected] or visit www.royalcyber.com.